Web App Pentest
Don’t let a vulnerability in your website compromise your entire IT stack. Secure your business with TAC Security VAPT
More than 95% of the websites have at least one vulnerability. Find your vulnerabilities and remediate them before they cause damage to your business. Also, get reliable audits and patch verifications now!
5+ Million
Vulnerabilities ManagedTop 10
Of the Fortune 500 Companies Secured2
Of the World’s Largest Governments Secured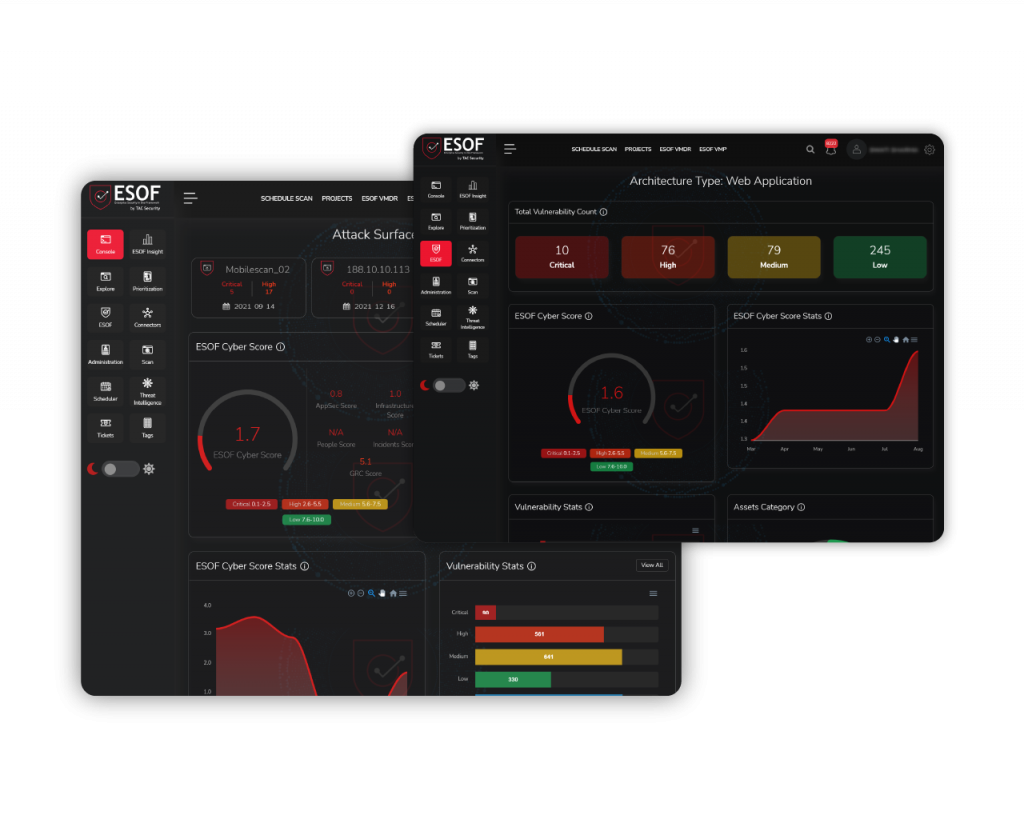
Choosing the wrong pentest partner can damage your reputation and cost you millions
Create a trustworthy brand, protect your business, and comply with international standards.
The significant and essential step is to get Pentest to fix all the faults in your business.
However, selecting the wrong Pentest partner could cost you valuable progress and reputation.

Brands worldwide trust TAC Security to identify the gap in their surveillance.

Comprehensive Scanner
Our VAPT team performs in-depth scans and finds the problem which other pentester generally miss out on.
Collaborative Dashboard
Consistently cooperate with your team members, CXOs, and our security expertise
Experienced Team
Discover and remediate security gaps in your cloud arrangement.
Real-time expert support
Get assistance from our security professionals inside your dashboards.
COMPREHENSIVE TESTING
Discover vulnerabilities that other pentests often miss in your web apps.
By leveraging creative hacker knowledge, TAC Security’s VAPT experts beat hackers at their own game.
Our VAPT service constantly evolves as our security professionals are up-to-date with the latest vulnerabilities.
Using your past pentest data, TAC Security customizes its scanner to work with your organization.
Smarter Vulnerability Analysis
OWASP/SANS Testing
Pentest your integral APIs
FOR DEVELOPERS
We’ll provide you with clear, actionable steps in detecting and fixing vulnerabilities by working together seamlessly.
CXOs and our security professionals consistently synergize with your team associates from our user-friendly control panel.
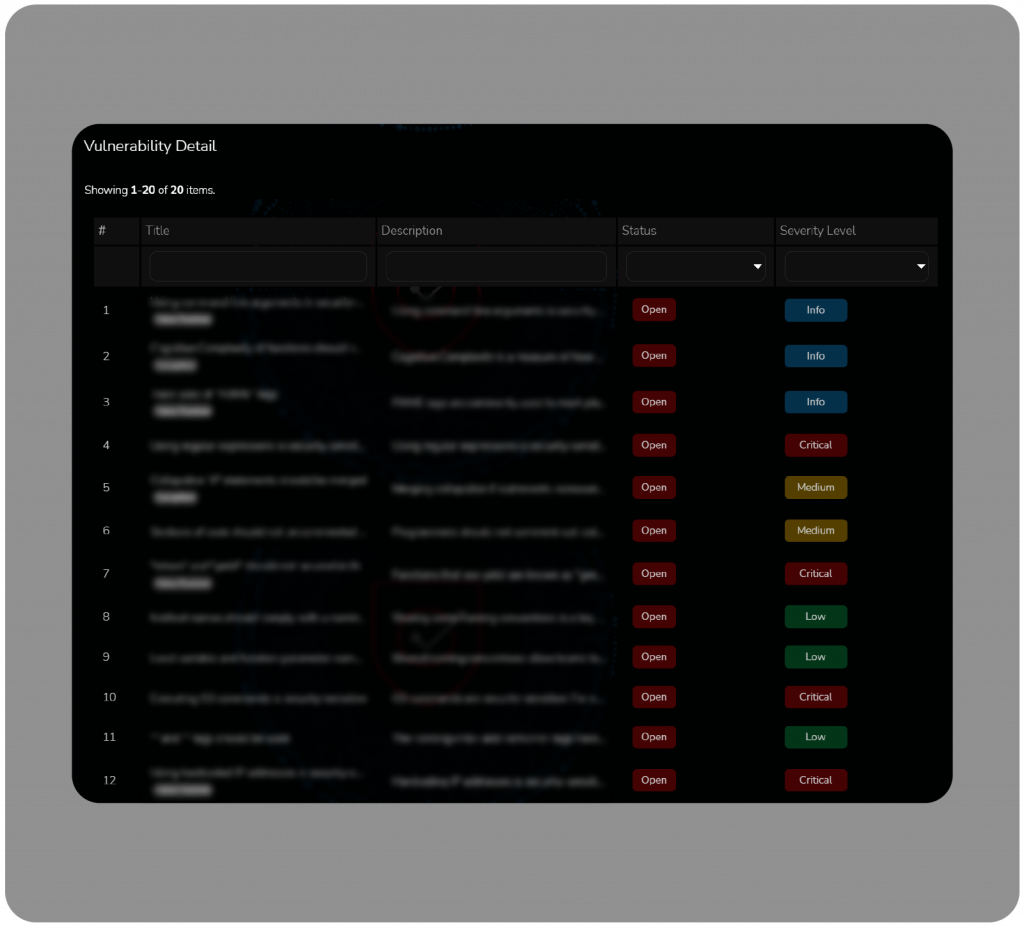
Check all the valuable details about every vulnerability in a single platform.
Be conscious about how you can imitate and test the vulnerabilities.
Get tailored, yet comprehensive step-by-step instructions to fix every vulnerability.
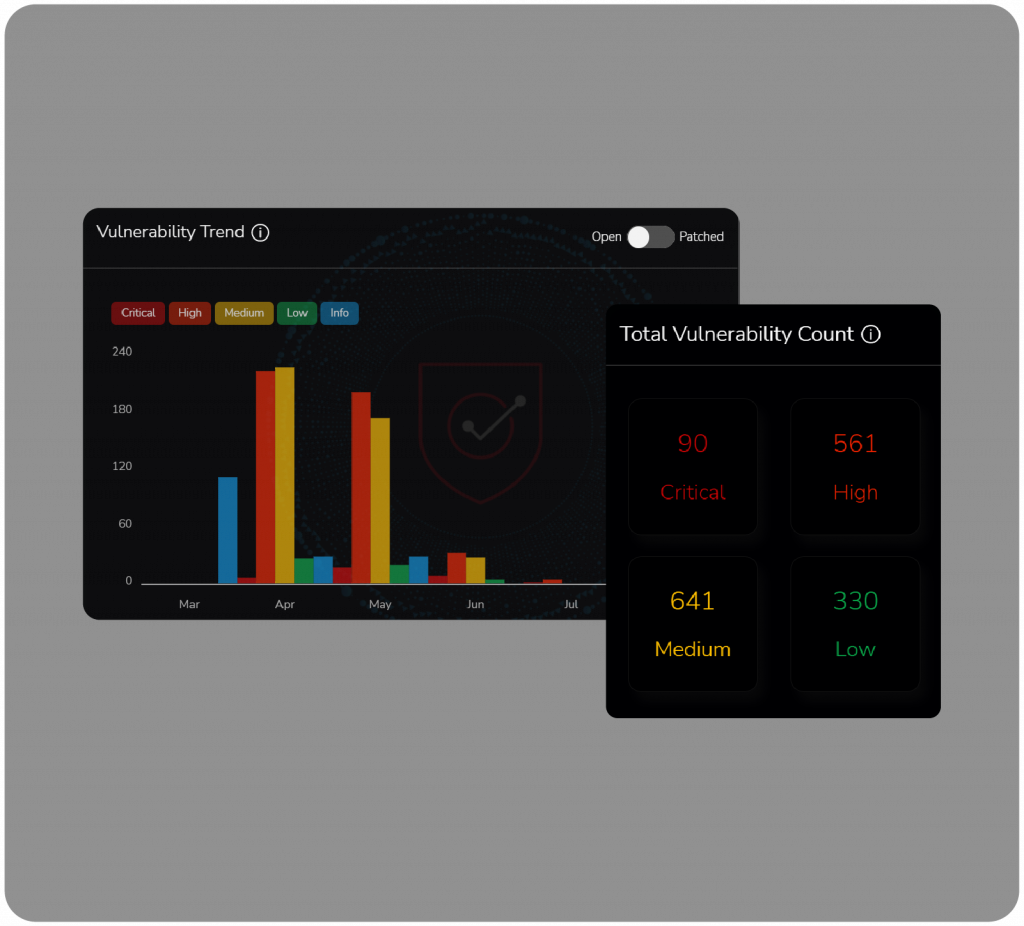
FOR CXOS
Track the enhancement with our CXO-friendly control panel and categorize the appropriate vulnerabilities.
Our CXO dashboard lets you see your security posture from a birds’ eye view.
Get to know the status without requiring to follow up
Utilize the developers’ time efficiently by prioritizing the proper fixes based on ROI.
Streamline your pentest process to move faster.

FOR COMPLIANCE
Acquire GDPR, CIS, and ISO consent equipped without any fuss.
TAC Security’s VAPT does all the significant tests necessary for you to attain HIPAA, SOC2, and GDPR compliance. Also, protect your IT stacks entirely and make sure that each vulnerability is removed.
INDUSTRY-RECOGNIZED CERTIFICATE
Win customer’s trust with a unique, publicly verifiable security certificate.
Establish trust with a unique, publicly verifiable security certificate. Make your application safe-to-host with a certificate, and have our engineers validate your fixes.
Build trust by sharing the certificate link with your partners and customers.


SUPPORT FROM EXPERTS
Our security professionals directly assist in fixing the vulnerabilities.
Pentesting shouldn’t drain your energy.
Get direct support from our security professionals.
Quick human support
99%
Satisfaction rate
Collaborate and connect with TAC Security for your current IT stack
Security issues can be tracked and collaborated easier with Vulnerability Assessment and Penetration Testing(VAPT).
For multiple vulnerabilities, get your web apps tested now!

Vulnerability Assessment & Penetration Testing (VAPT)
We examine your cloud infrastructure for any defects that could allow malignant users to access your system and destroy your fame and the customers’ trust in your firm. Also, we include all preeminent security standards, including CIS, OWASP, SANS, CREST, etc.
Server Infrastructure Testing & DevOps
In-depth scanning of the current structure, ensures encryption and protected data storage, enhances the DevOps method, and ensures that your data never gets ruptured.
Network Devices Configuration
We’ll evaluate the gadget patch level, register and inspect execution, and identification mechanisms, and run tests based on gadget composition, managerial and verification services, network filtering, and protocol analysis.

Payment Manipulation Testing
Detects all the faults in your vacate portals and payment gateways, secures your website from credit card hacks, price conduct vulnerabilities, and so on.

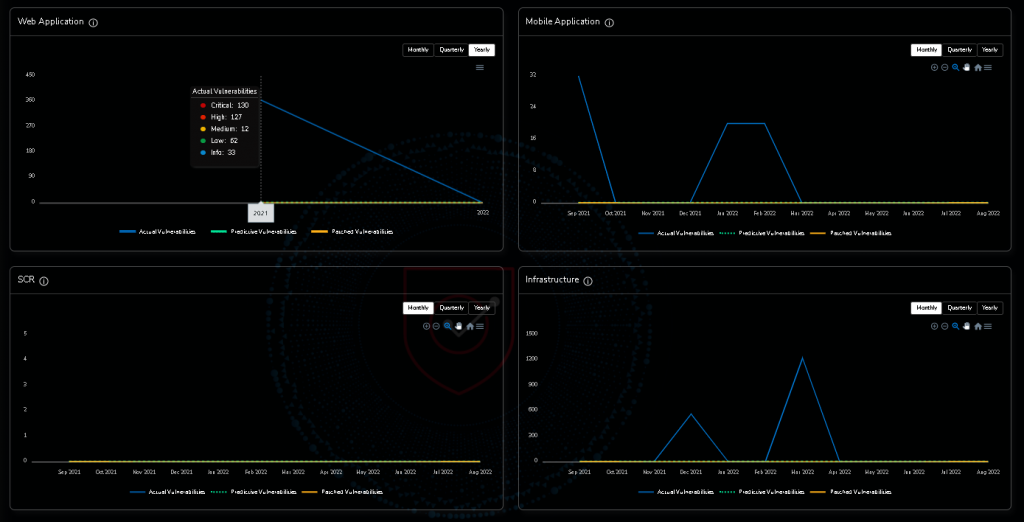
Keep in the loop with an intuitive dashboard
Watch the live reports of vulnerabilities and communicate with our expert professionals directly. Also, you can do the scheduled scanning after remediation, ensuring your website is protected.
Business Logic Testing
You are vulnerable to privilege escalation and price manipulation on your website. Your website might bypass Security restrictions, and hackers could access unauthorized information. We examine business logic testing and many more.

Patch up vulnerabilities
Get to know what is needed to enhance your website and protect it fully. Also, we’ll provide you with informative reports with proper steps PoC and brief details on how to maintain your security posture with VAPT.
Keep in the loop with an intuitive dashboard
Watch the live reports of vulnerabilities and communicate with our expert professionals directly. Also, you can do the scheduled scanning after remediation, ensuring your website is protected.
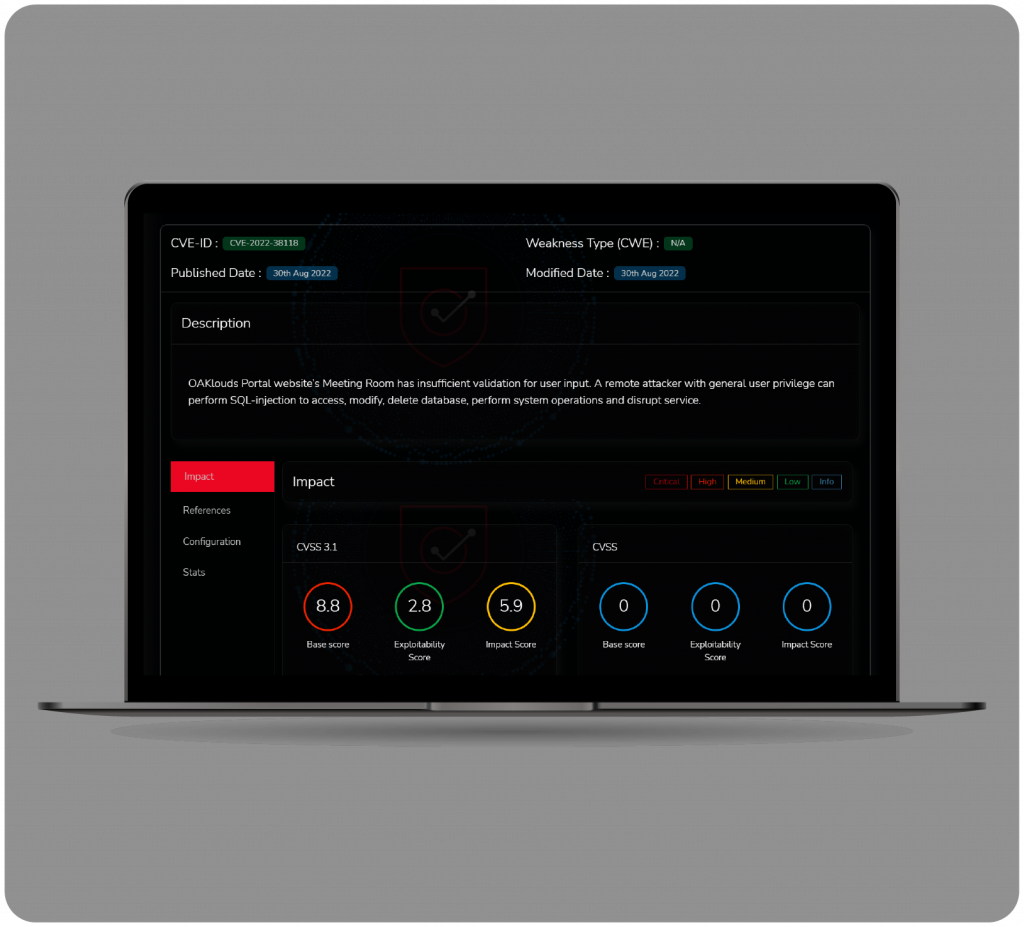
Test for known CVEs
Scheduling scan penetration testing can identify any security defects and vulnerabilities that hackers could exploit.
Find every threat to your web apps in record time, with TAC
Copyright © 2022 TAC Security, Inc. All Rights Reserved.









