Vulnerability Management is the continuous process of identifying, assessing, prioritizing, mitigating, and remediating the vulnerabilities across the complete IT infrastructure of the organization. Cybersecurity needs to be monitored in real-time and remediated as soon as possible to avoid attacks, this activity is often overseen by organizations through vulnerability management tools or products.
Organizations often misunderstand Vulnerability Management as the act of patching and reconfiguring uncertain settings; however, it’s more than just repairing the glitches and gaps. It is a disciplined process that needs to be constantly scrutinized and evolved, keeping in mind that vulnerabilities and risks occur and are found daily and need real-time discovery, prioritization, and remediation to be secure.
What is the difference between Vulnerability Management and Vulnerability Assessment?
Often Vulnerability Management and Vulnerability Assessment are misunderstood to be the same thing but the latter is only a portion of the Vulnerability Management process, where there is a one-time assessment of the vulnerabilities discovered and to place the Vulnerability Management process in motion.
While vulnerability assessment is a part of vulnerability management, the vice-versa is not true.

Picking the right Vulnerability Management Process
Pre Vulnerability Management
Before you choose a vendor, a couple of internal allocations should be made. Such as defining the scope and goal, allot responsibilities, listing down tools that match requirements, drawing a list of the assets that have to be assessed, etc.
This will help you make a more suited and informed decision and would clear out the scope of work for the vendors as well to ensure they become an asset instead of an additional effort.
While Choosing the Vulnerability Management
Be sure to ask your vendors the following questions while choosing the product –
- What are the reporting methods?
- What are the assessment timelines?
- Do the assets have to have downtime while their assessment proceeds?
- How invasive is their tool?
Vulnerability Management
The Vulnerability Management process can be broken down into the following steps –
- Identifying and assessment
- Prioritize and Remediation
- Reporting and cyberscore
Step 1 – Identifying and assessment
The vulnerability management process begins with identifying every single vulnerability available across the organization, including the applications, infrastructure, endpoints, software, etc.
Often while these scans, a lot of networks become unstable or behave erratically when scanned, they might need to be excluded from vulnerability scans, or the scans may need to be fine-tuned to be less unstable. Some of them may even slow down the company’s infrastructure which may cause work delays internally and externally, to avoid this, they have to be scheduled at alternate hours that allow the systems to be down yet monitored.
After the scanners produce a report with what possibly could be millions of vulnerabilities across the entire network, it is then left to the IT team to go through them and prioritize the important ones. A manual process that is not necessarily an accurate one.
Step 2 – Prioritize and Remediation
After the scanners produce a report with what possibly could be millions of vulnerabilities across the entire network, it is then left to the IT team to go through them and prioritize the important ones. A manual process that is not necessarily an accurate one.
This often makes the remediation process an elaborate one as the team has to find a needle from a haystack to decide which ones to prioritize first. The other cause of delay is a lack of knowledge or experience of how to remediate a particular vulnerability. The time is then invested in research and development which leaves the vulnerability open for longer than permissible, leaving the organization prone to attacks.
Step 3 – Reporting and Cyberscore
Vulnerability Management is a continuous process, ideally done in real-time. The constant reporting allows the organization to prepare for the attacks and improve its cybersecurity process.
The reassessment after remediation allows the teams to align and report the improved status and security levels of the IT infrastructure. This allows the IT teams, the business side of the organization, CISO, and Board Members to understand the details and allocate budgets.
Cyberscore is the Future of cybersecurity.
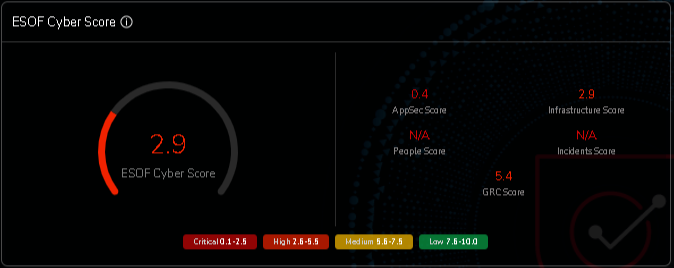
As per the future of cybersecurity, cyber scores are an essential part of it as they help different units of the organization understand where exactly they stand on their security levels.
Conclusion
The attack surface of an organization changes and expands every day as they introduce new employees, assets, partners, servers, etc to the system making it vulnerable. To monitor and protect your organization, a Vulnerability Management system that gives real-time cybersecuring abilities is a need of the hour.
Request a demo to understand your Vulnerability Management needs better.

