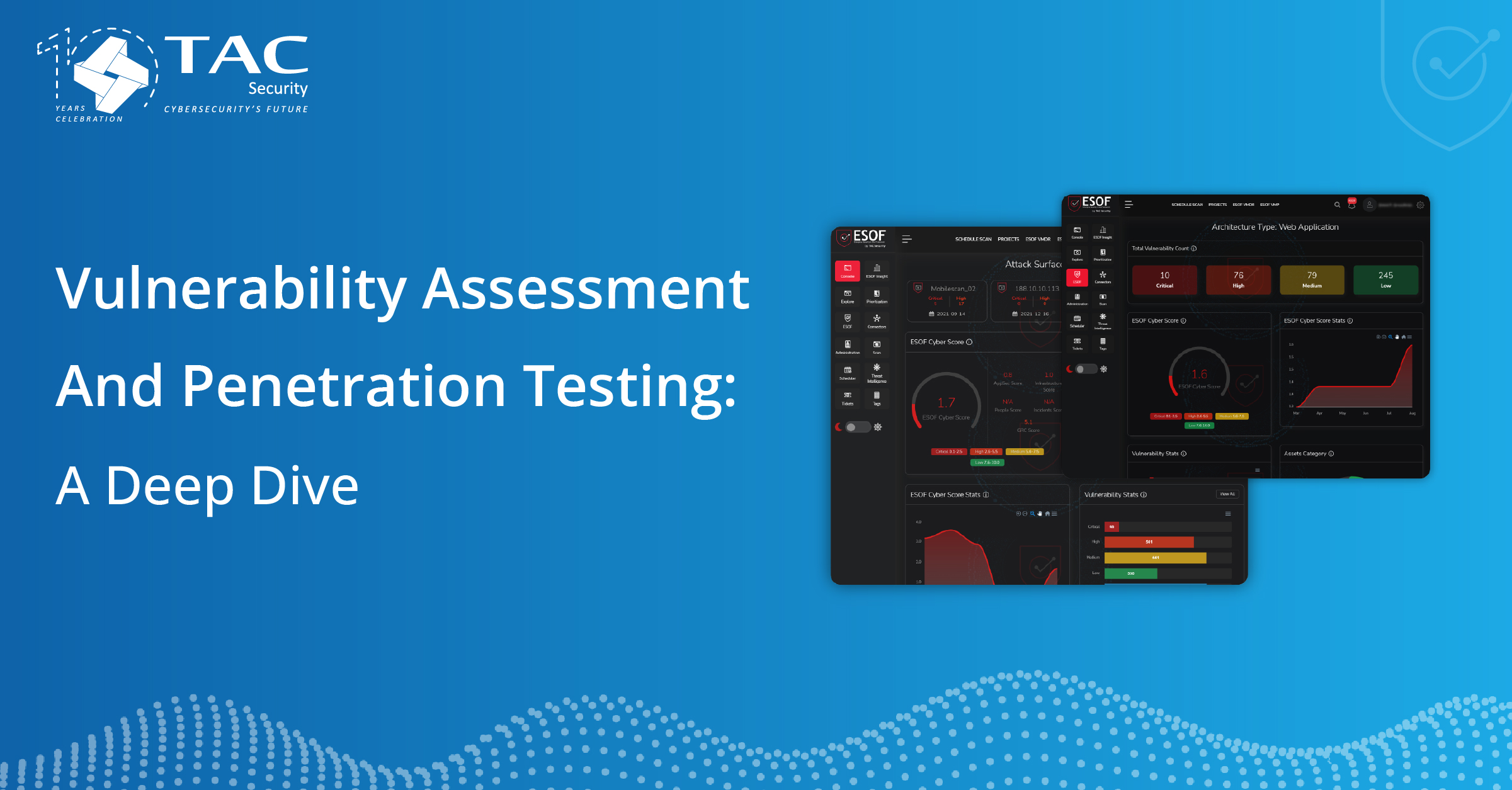
In today’s digital age, your website is often the first point of contact between your business and potential customers. However, it’s essential to recognize that more than 95% of websites have at least one vulnerability. These vulnerabilities can compromise your entire IT stack and damage your reputation. That’s where TAC Security’s Vulnerability Assessment and Penetration Testing (VAPT) services come into play.
Why VAPT Matters
Choosing the right VAPT partner is critical for securing your business, protecting your brand, and complying with international standards. A vulnerability in your website could cost you valuable progress and reputation, making comprehensive testing a necessity.
Comprehensive Testing
TAC Security’s VAPT experts are dedicated to discovering vulnerabilities that other penetration tests often miss in your web applications. They leverage their creative hacker knowledge to beat hackers at their own game. Our VAPT service is continually evolving, with our security professionals staying up-to-date with the latest vulnerabilities.
Using your past penetration test data, TAC Security customizes its scanner to work seamlessly with your organization. For developers, we provide clear, actionable steps for detecting and fixing vulnerabilities. Our CXOs and security professionals collaborate seamlessly with your team associates through our user-friendly control panel, providing all the valuable details about every vulnerability in a single platform.
For CXOs
Our CXO-friendly control panel allows you to track enhancements and categorize vulnerabilities efficiently. You can see your security posture from a bird’s eye view, eliminating the need for constant follow-ups. By prioritizing the proper fixes based on ROI, you can utilize your developers’ time efficiently and streamline your penetration testing process to move faster.
For Compliance
Achieving compliance with regulations like GDPR, CIS, and ISO is no longer a hassle. TAC Security’s VAPT service performs all the necessary tests to help you attain HIPAA, SOC2, and GDPR compliance. Protect your IT stack entirely and ensure that every vulnerability is addressed.
Industry-Recognized Certificate
Win your customers’ trust with a unique, publicly verifiable security certificate. Establish trust by making your application safe-to-host with a certificate, and have our engineers validate your fixes. Share the certificate link with your partners and customers to build trust and demonstrate your commitment to security.
Support from Experts
Penetration testing shouldn’t drain your energy. With TAC Security, you get direct support from our security professionals. We provide quick and reliable human support, with a 99% satisfaction rate, ensuring that you have the assistance you need to secure your IT stack.
Collaborate and connect with TAC Security for your current IT stack. With Vulnerability Assessment and Penetration Testing (VAPT), security issues can be tracked and resolved more efficiently than ever before.





