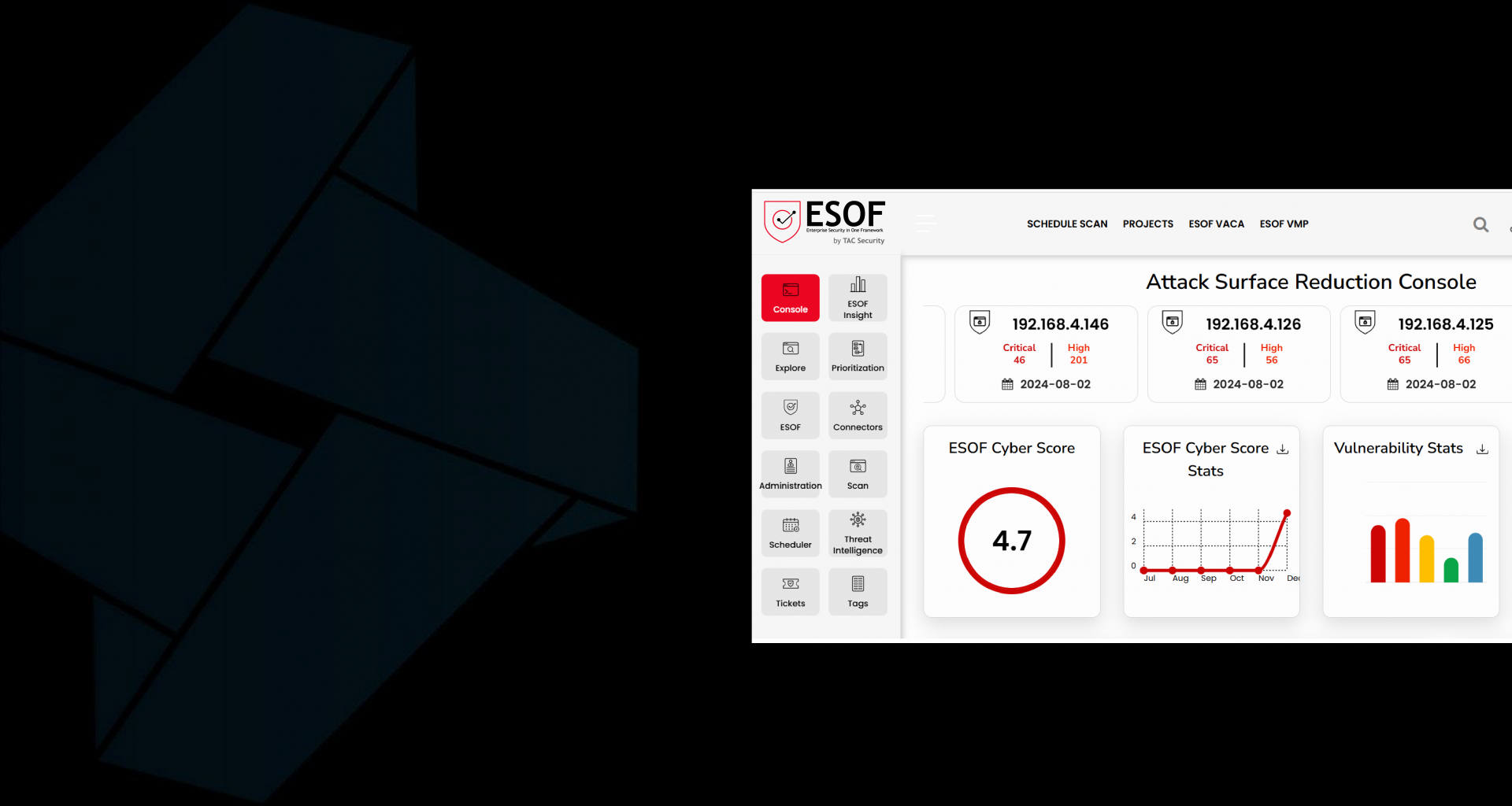
SINGLE CYBER SCORE
-
1.8 -
PEOPLE SCORE
-
INCIDENT SCORE
-
INFRA SCORE
-
APPSEC SCORE
-
RISK SCORE
See for yourself.
Try ESOF VMP.
No software to download or install.
Email us to request a quote or fill the form.
HOW ESOF WORKS
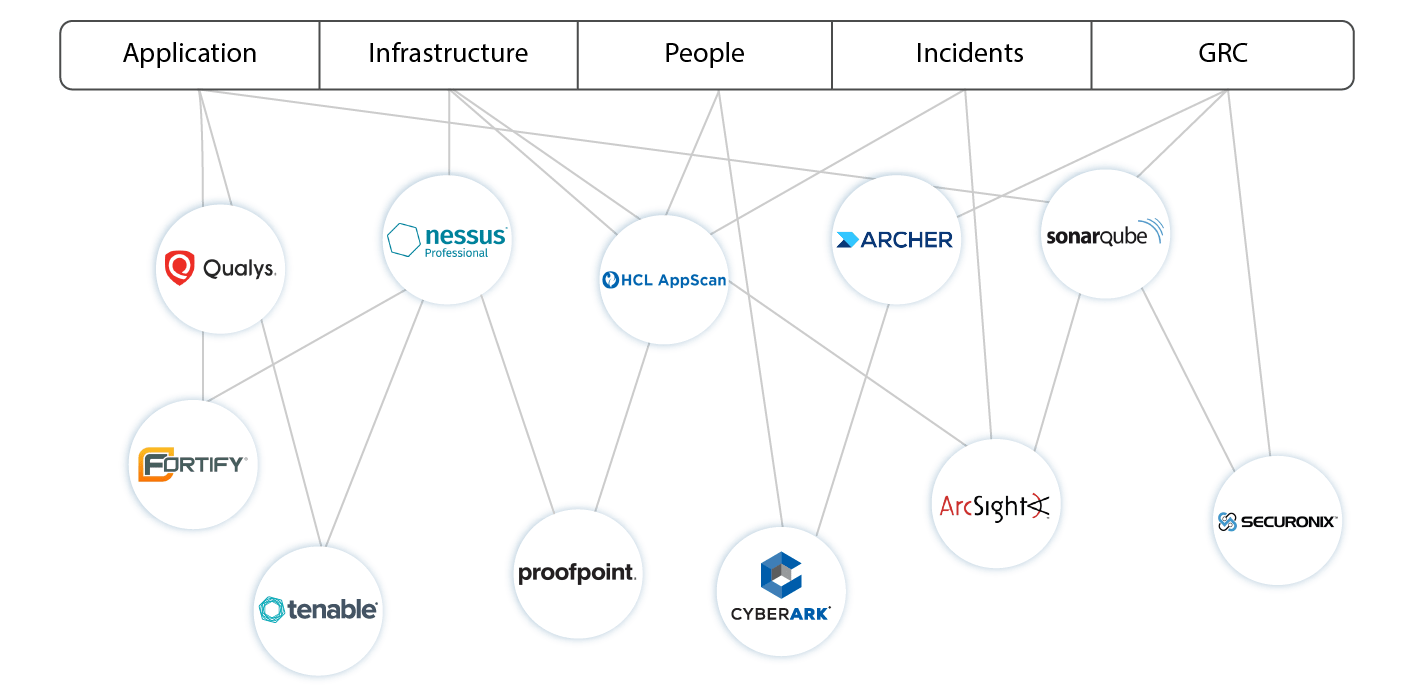
Multiple Tools
Organizations use multiple tools to maintain their complete IT stack. This often does not give a complete picture of your security levels and does not allow you to prioritize your vulnerabilities to manage the risks.
Data onboarding
ESOF gives you the widest coverage on a single platform. You can now manage your entire IT stack in one place allowing you to prioritize, manage and mitigate effectively. Our onboarding process is seamless and does not require you to pause operations.
Multiple Business Units & Tech Team
It is difficult to align various teams, run multiple drill downs and effectively manage your vulnerabilities to eliminate the risks. With ESOF, everyone is updated with the latest status, see the score, connect with the team via the ticketing system, etc
Prioritization
ESOF helps you in prioritizing your vulnerabilities and vulnerable assets by the severity, enabling you to mitigate them effortlessly. Risk management at its best!
Remediation
Why invest time and money in finding a solution when we have one?
Our 5million+ playbook of vulnerabilities enables us to give you a remediation tailored to your environment and needs. Hence, instead of finding a solution, you eliminate the risk.
Data On – boarding
– App Scan Tool Integration
– Infra Scanning Tool Integration
– Penetration Testing Report
– Security Audit Report
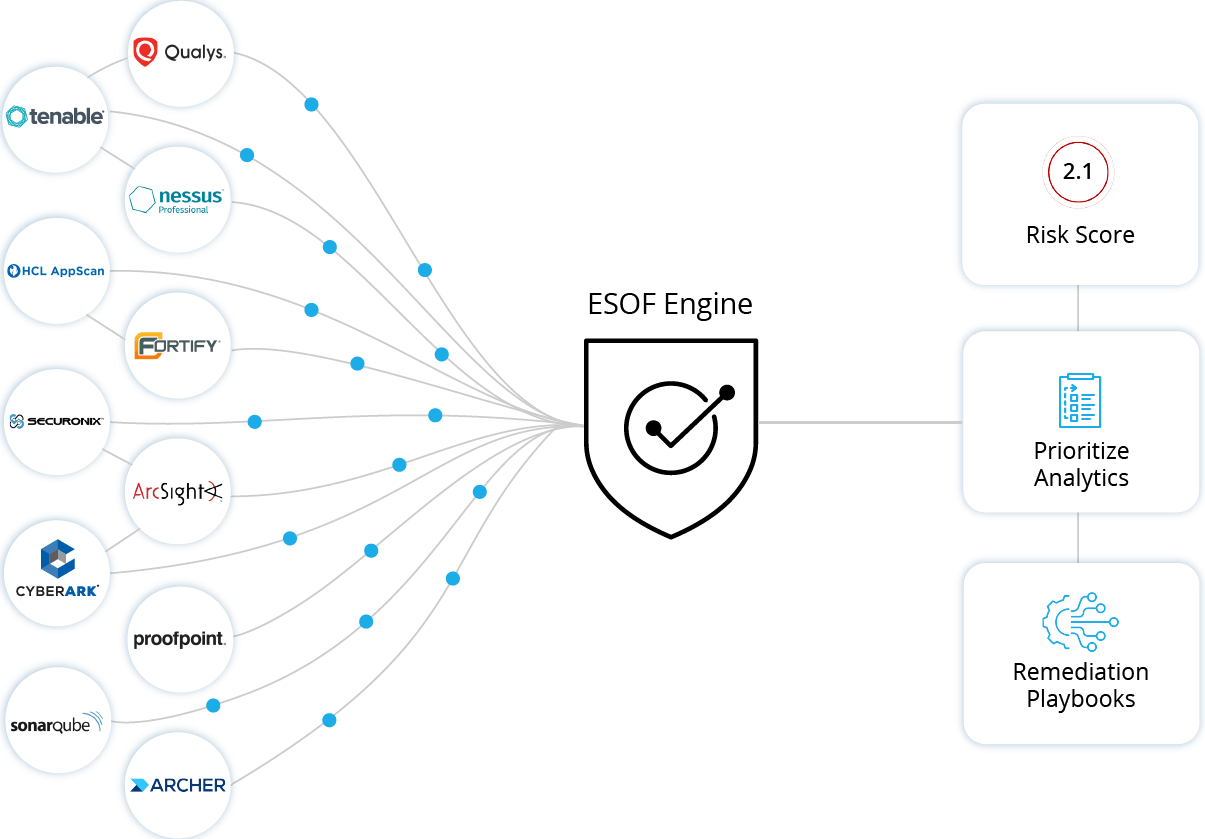
ESOF Engine
ESOF uses remediation playbooks to prioritize the risk of your business and gives you an accurate result along with a cyber-risk scoring based on the help of AI and machine learning, while it helps in saving time.

Tech Assets Data
Database Assessment Reports –
Configuration Assessment Report –
Source Code Bugs –
Policy Review –

Cyber Score
An Artificial Intelligent Algorithm calculates the score based on the type, severity and total number of vulnerabilities found.
Intelligent Remediation
ESOF’s remediation playbook helps an organization to automate the process of presenting the tailored remediations while improving the security posture.

Prioritization
ESOF enables an organization to quickly present the most critical assets and vulnerabilities exisiting that helps to prioritize and enable a rapid mitigation.
World’s Top Brands Trust Us!





Customer Success Stories.
A glimpse into how we’ve empowered
organizations to secure their people,
infrastructure, and other vulnerable surfaces.
See for yourself.
Try ESOF VMP.
No software to download or install.
Email us to request a quote or fill the form.