Already have an Account?
Power-Driven by the ESOF Cloud Platform

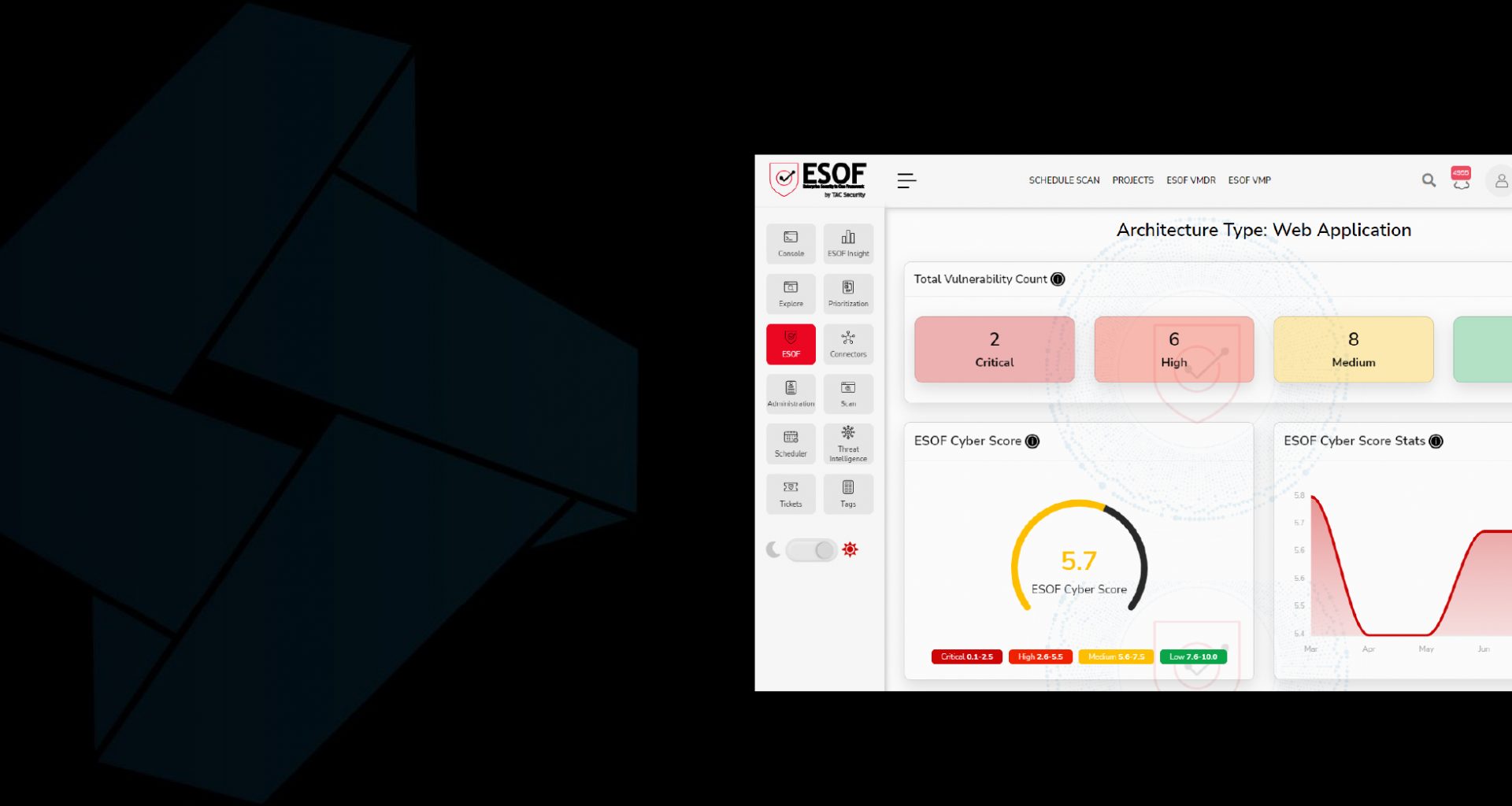
Comprehensive Scan
Powered by advanced technologies, the ESOF AppSec Scanners perform Black Box and Grey Box Testing to accurate app test results.

Intelligence-Powered Application Scanning
Deep scans enabled within the ESOF AppSec software make use of cyber threat intelligence to provide detailed information of web, mobile, and API vulnerabilities in addition to malware discovery.

Coverage of OWASP Top 10 and SANS 25 Vulnerabilities
Get all the application vulnerabilities validated by OWASP and SANS detected, scanned, patched, and rescanned automatically within the platform to ensure the protection of your application systems.

SDLC Embedded with Security
Apart from being compliance-ready, let your apps undergo penetration tests throughout the entire Agile or DevSecOps lifecycle to get them rid of flaws, thereby, veiling every endpoint from where they can be inherited into the IT network.
ESOF AppSec Features
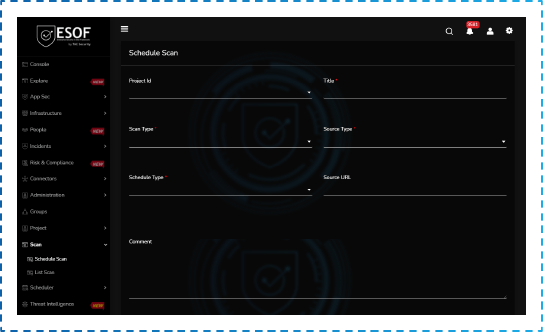
Scheduled Scans
Scans can be scheduled for daily, weekly, monthly, bi-annually, or yearly, and can be done immediately after acquiring the ESOF AppSec License
Zero False Positives
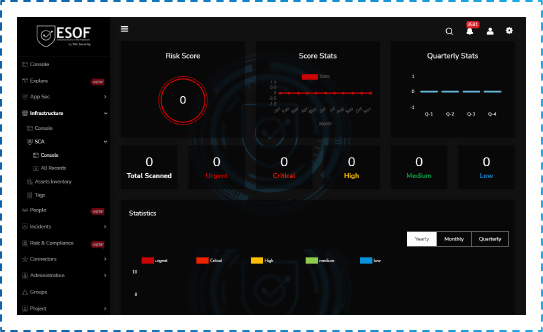
Our next-generation scanning engine discovers all vulnerabilities for the in-scope assets. We evaluate in detail the attack surface of the assigned assets by automated and manual testing and provide evidence of the vulnerabilities found.
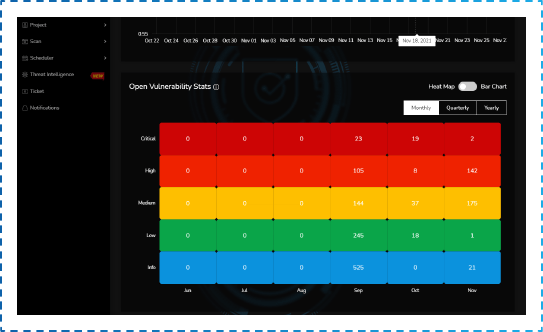
Vulnerability Timeline
The ESOF-AppSec vulnerability timeline gives you visibility of all open and patched vulnerabilities since the initial scan so you can focus on immediate threats to your business and align your teams for efficient mitigation results.
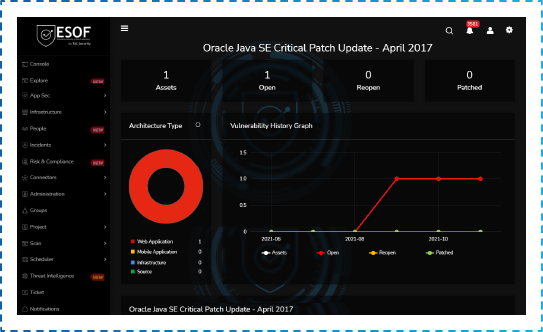
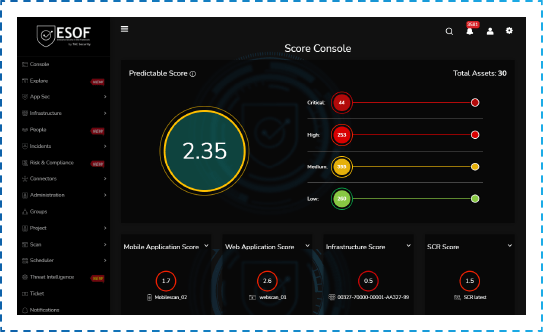
ESOF Cyber Risk Score
ESOF’s Cyber Risk Score helps to measure the risk of your application with the help of artificial intelligence and provides a single score that allows you to explain the security posture to business owners and reduce the cyber risk on a real-time basis.
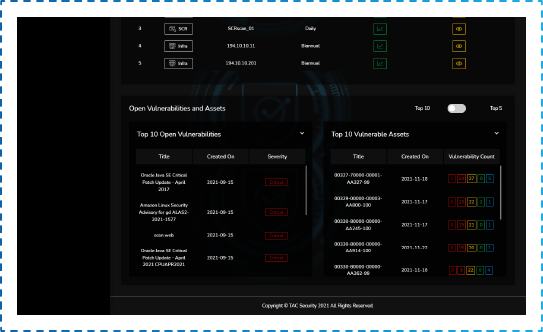
Top 10 Vulnerabilities and Top 10 Vulnerable Applications
We solve one of the frustrations with finding too many vulnerabilities. ESOF-AppSec provides a standard report of the Top 10 Vulnerable Applications Vulnerabilities based on the number and the severity found. This helps to align the organization to use its resources effectively.
History Trend
ESOF’s history reporting helps you present the improvement and the progress of the organization’s IT Security posture from the day it was onboarded, with up to 5 years of history.
Sign up ESOF AppSec by TAC Security
ESOF AppSec –
Advanced
$ 900
per application
What’s included
- Application Security Assessment – Yearly
- Support for Vulnerability(s) Remediation
- 2 Cycles of Revalidation
- DAST
ESOF AppSec –
Premium
$ 1800
per application
What’s included
- Application Security Assessment – Biannually
- Unlimited Automated Vulnerability(s) Revalidation
- Manual Vulnerability Assessment & Penetration Testing by Certified Security Experts ( up to 2 revalidation scans per asset biannually)
- Executive Summary Report
- DAST
ESOF AppSec –
Enterprise
Quote on Request
What’s included
- Application Security Assessment – Unlimited
- Unlimited Vulnerability(s) Revalidation
- Manual Vulnerability Assessment & Penetration Testing by Certified Security Experts
- Dedicated Account Manager
- CREST PT Certified Report
- Executive Summary Report
- DAST & SAST
Already have an Account?
Get your App’s Cyber Score at Instant Disposal!
Get your hand on ESOF AppSec.
Drop us a quote or fill the form.
With ESOF AppSec’s Extensive Range of Web Application Security Testing,
Rest Assured of Compliance, DevSecOps Improvement, and Business Security.

Web Application Testing
Our exhaustive penetrating testing is well-targeted in discovering threats and dangers to the applications and acts deliberately over the inadvertent actions and exposure points, thereby, closing loops for any exploitation type.

Mobile Application Testing
Our all-in-one solution guarantees to test applications in static and dynamic environments across both iOS and Android devices and detect privacy issues and security loopholes, scanning the entire mobile app source code.

Source Code Review
An array of human inspections and automated reviews, together ensure and make certain the augmentation of the source code security by identifying weaknesses across the entire code, and thus, eliminating security flaws and business logic errors.

Looking for Manual Application Penetration Testing?
End your search for self-assessment and external assessment of your applications via our all-in-one ESOF AppSec solution combined with professional services that can serve with Penetration Testing, Business Logic Assessment, Vulnerability Assessment, and much more.
World’s Top Brands Trust Us!
REAL CUSTOMERS. REAL STORIES.
See how we’ve helped industry leaders secure their teams, products, and attack surfaces.
Book a Demo!
Email us to request a quote or fill the form.