ESOF VACA
TAC Security’s agent-based scanner offers vulnerability management, detecting vulnerabilities and misconfigurations in your Linux and Windows systems.
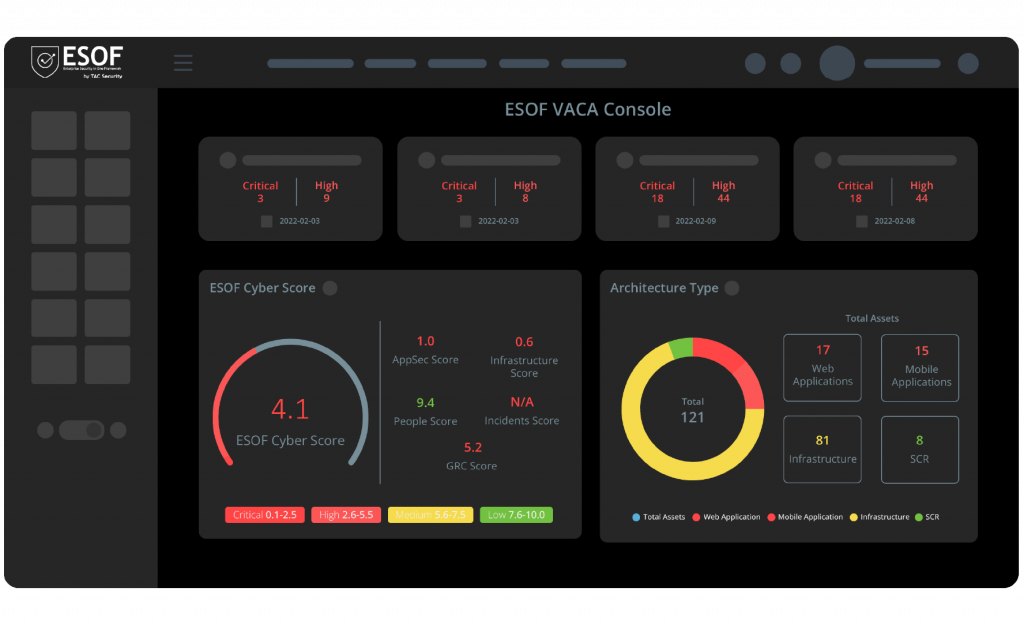
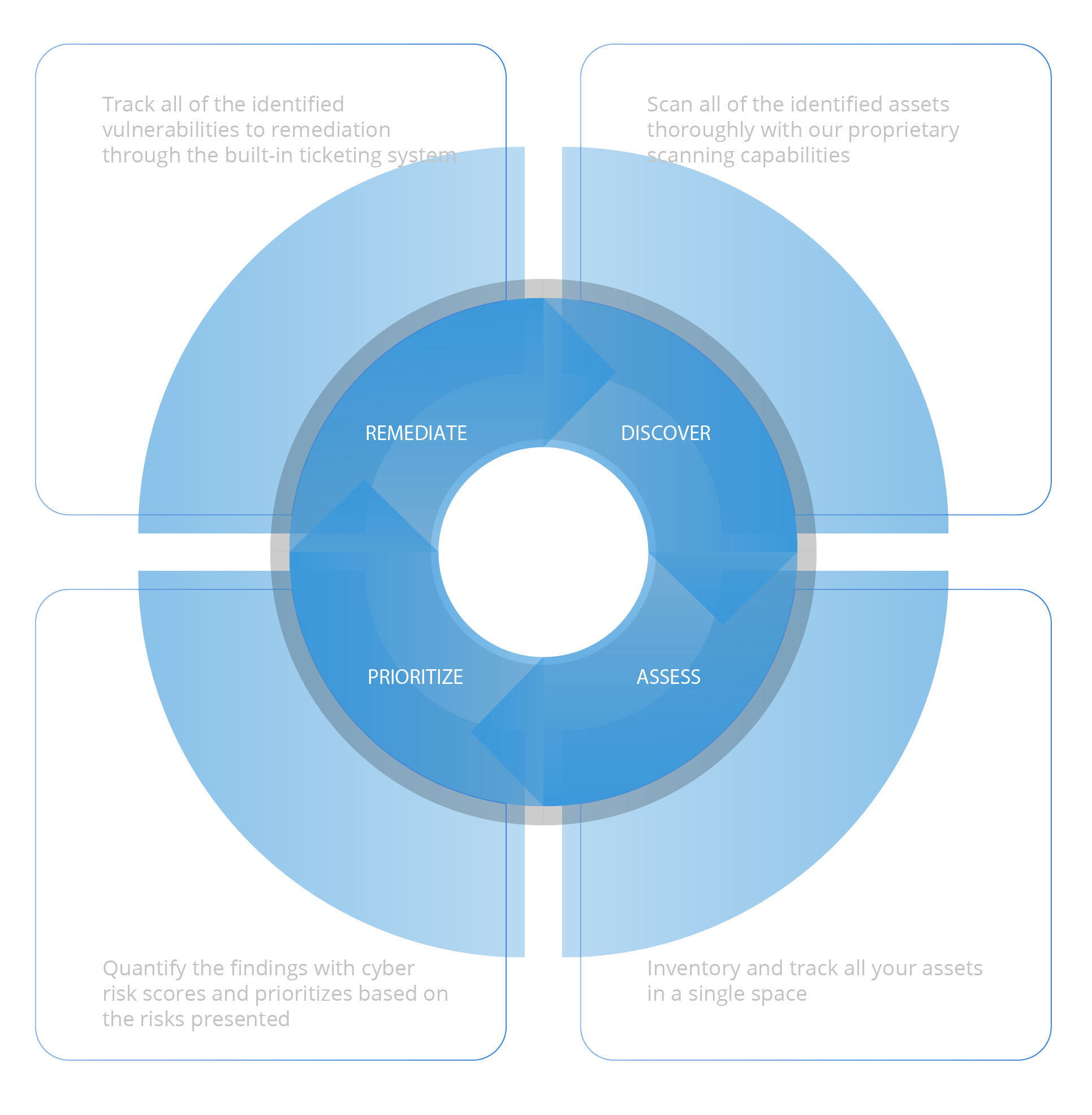
ESOF VACA with end-to-end automation capabilities
An innovative, single platform that discovers, evaluates, categorizes, and responds to vulnerabilities throughout an entire system while calculating a cyber score.
The ESOF vulnerability scanner continuously scans and detects asset threats, vulnerabilities, and risks. Also, ESOF VACA does the intel analysis to prioritize exploitable risks, catch the latest superseding patch for the vulnerable asset, and deploy remediation quickly.
ESOF VACA allows forward-looking enterprises to do the vulnerability analysis of every asset within their IT infrastructure automatically without the need for any human intervention, which includes refractory assets, hardware/ software inventory, and so on. Once identified, these assets are tagged, and communication is done with the team for better vulnerability Assessment.
Make the switch to ESOF VACA
Comprehensive coverage on a single platform.
Next-generation VM combines legacy VA plus multiple security tools (Application security, Full lifecycle vulnerability management platform, Threat Intelligence, Cyber risk quantification etc.).
Most Affordable
We charge on a pay-as-you-go model where assets can either be added or subtracted based on the customer’s requirement. We support businesses and organizations of various sizes to ensure we support everyone’s cybersecurity efforts.
Easily Deployable
As a SaaS platform, the only requirement from the customer’s end would be to install the agent on the scoped systems. Scanning and tracking all the vulnerabilities are extremely effortless
Best in class support and expertise
With ESOF VACA, you not only gain the competence of a state of the art vulnerability and configuration assessment scanner but also the expertise and support of a decade-old cybersecurity firm’s proficiency
Why choose ESOF VACA?
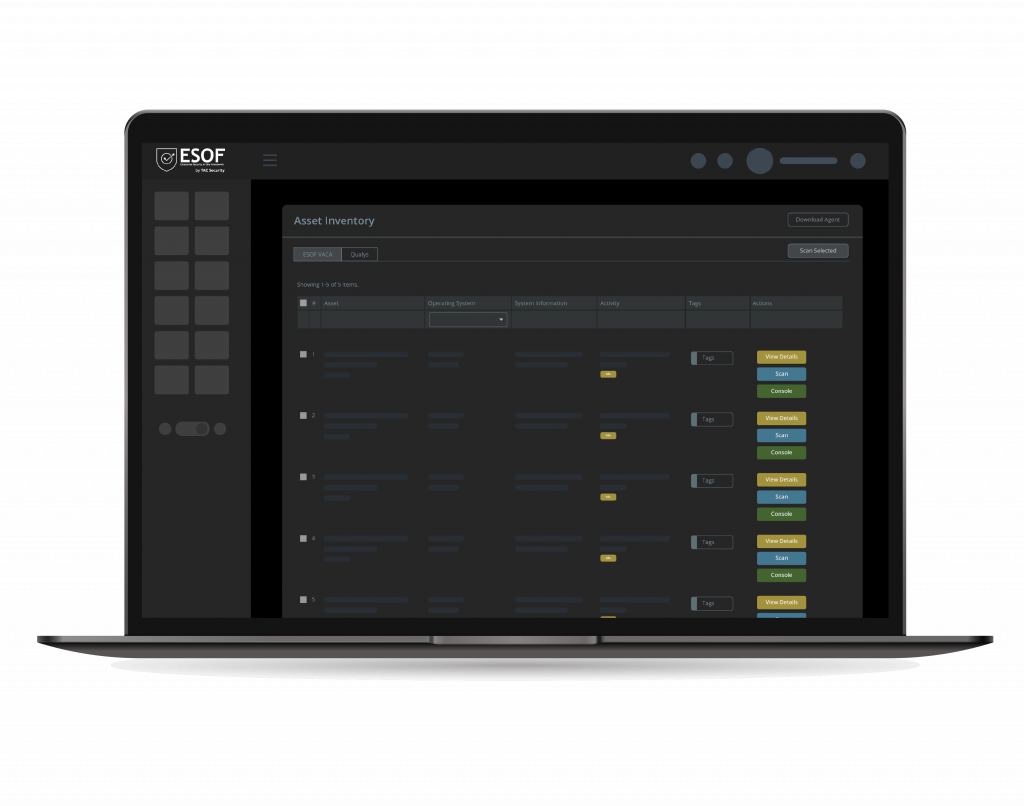
Asset Management
The Asset Inventory provides a real-time record of all your assets in a single place, enabling organizations to classify, track, and assess them. This ensures complete visibility, simplifies vulnerability management, and enhances comprehensive security. It integrates with other security tools, aiding in effective asset tracking and compliance checks.

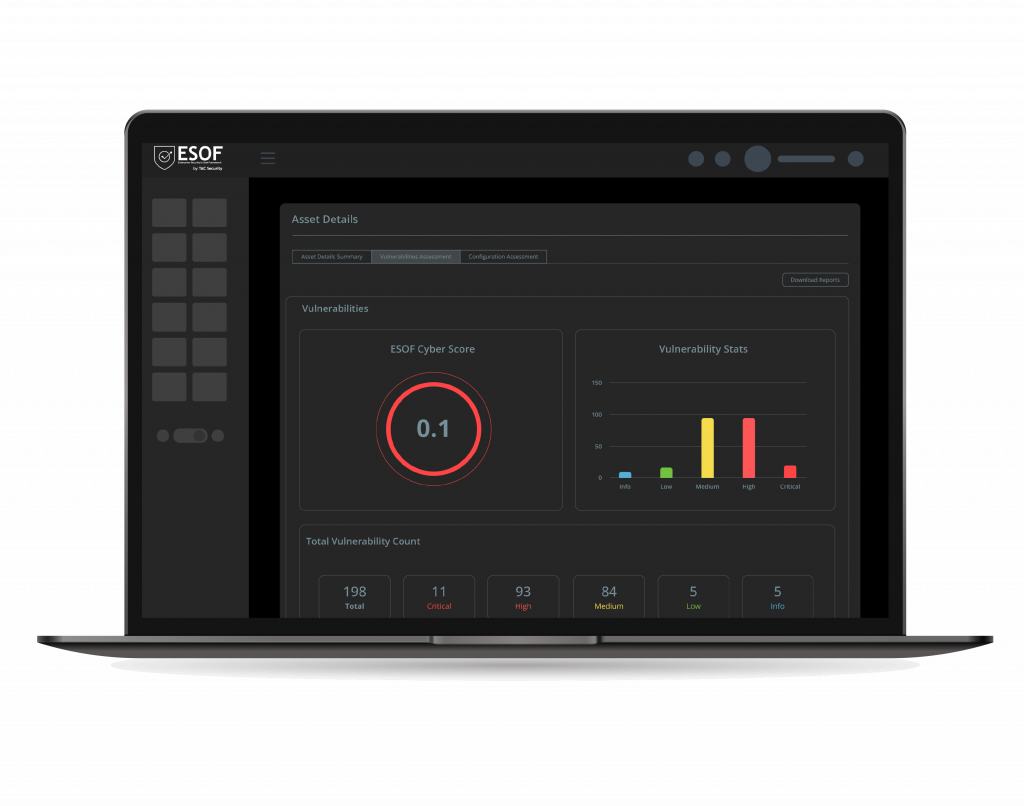
Vulnerability Assessment
Elevate your cybersecurity with comprehensive Vulnerability Assessment for both Windows and Linux systems. Unveil hidden weak spots in your digital infrastructure, safeguarding your business around the clock. Our cutting-edge assessment scans, pinpoints, quantifies and prioritizes vulnerabilities swiftly, ensuring your systems remain impenetrable. Opt for our Vulnerability Assessment and fortify your Windows and Linux systems today!
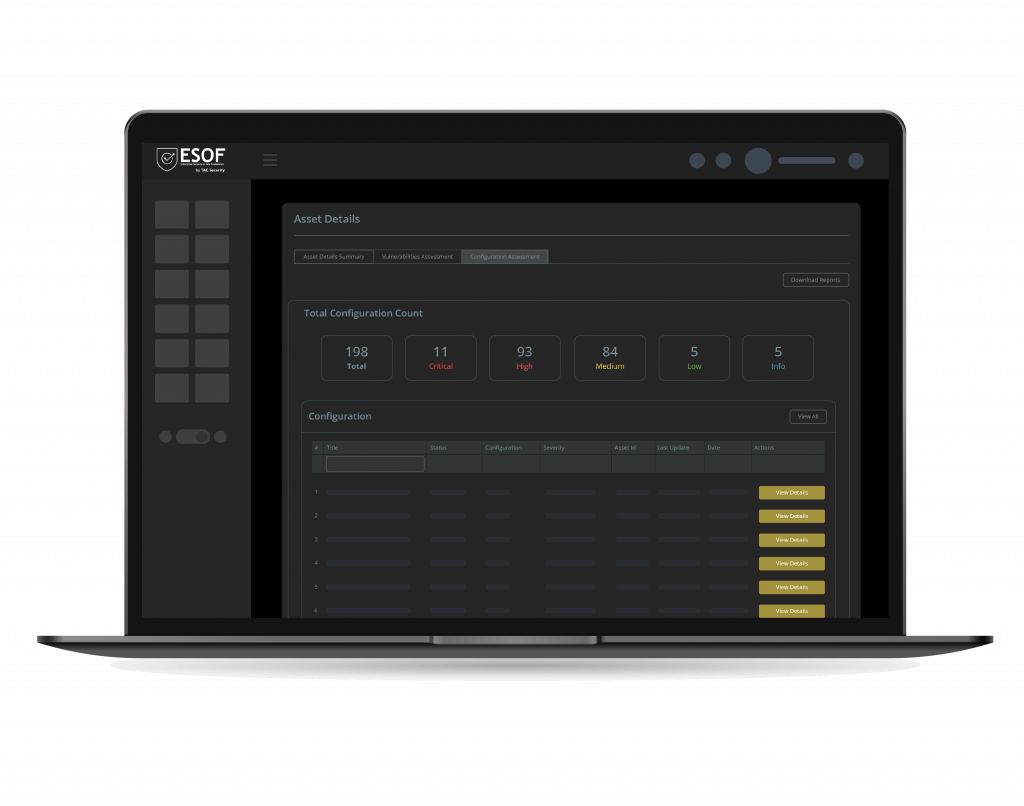
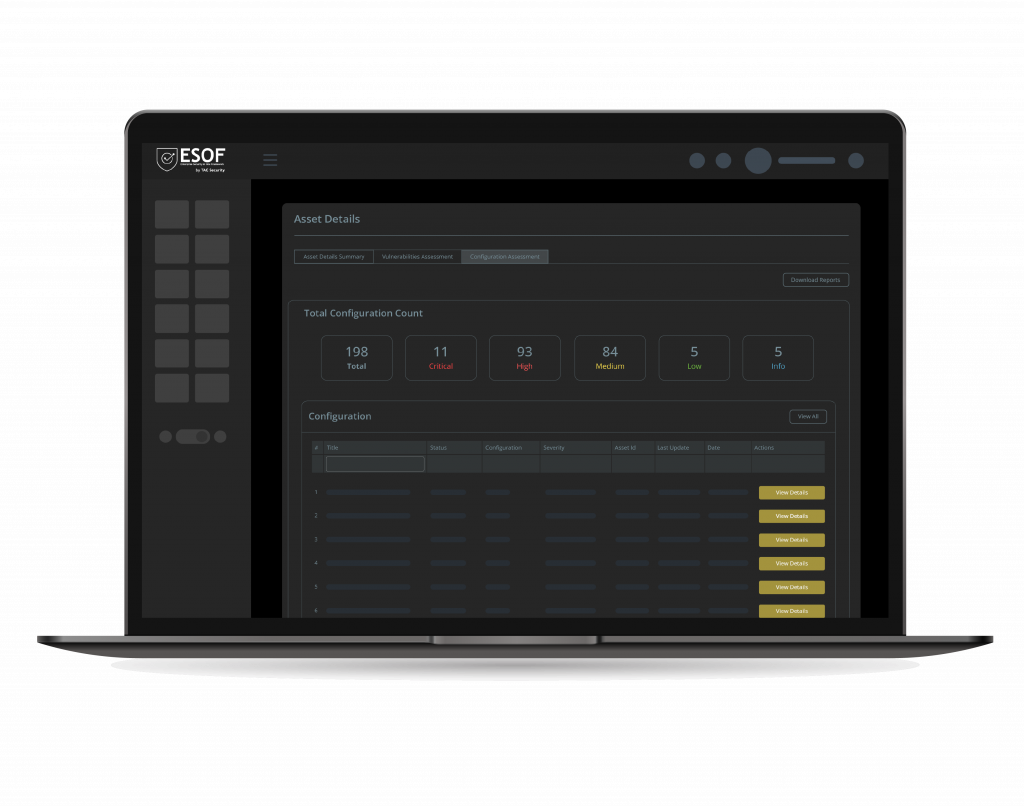
Configuration Assessment
Our Configuration Assessment module meticulously inspects and evaluates the settings and configurations of your linux and windows environments, ensuring they align with CIS benchmarks. VACA helps keep your infrastructure robust, efficient, and resilient. Detect misconfigurations and vulnerabilities before they become liabilities.

Threat Intel and Zero Day Vulnerabilities
VACA is fortified with state-of-the-art Threat Intelligence and Zero-Day Vulnerabilities capabilities. With real-time Threat Intelligence, you receive immediate alerts and insights about emerging threats, enabling proactive defenses.
Additionally, our scanner is equipped to detect Zero-Day Vulnerabilities, the elusive weaknesses that are yet unknown to the public or even software vendors. By pinpointing these vulnerabilities, you can patch or mitigate them before malicious actors exploit them.
ESOF CRQ (Cyber Risk Quantification)
With precise measurement and analysis, we translate complex security data into tangible financial metrics, helping you understand and prioritize your organization’s cyber risks.

Asset Summary Details
Get a glimpse of all crucial information about your system such as system info, network info, open ports lists, and the list of installed software for all assets in your inventory.
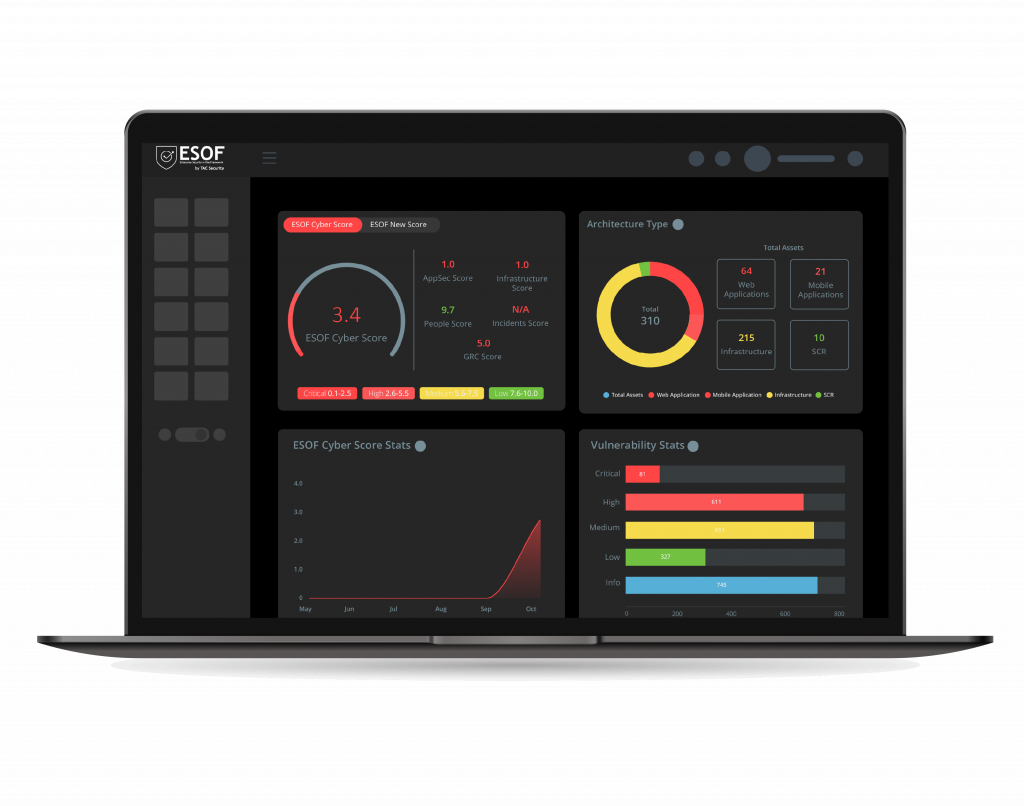
ESOF Cyber Risk Score
The ESOF Cyber Risk Score by TAC Security is your quick and accurate gauge of cyber risk. It assesses vulnerabilities, exposures, and threats, translating them into a actionable metric. With this score, you can make informed decisions to bolster your cybersecurity and safeguard your digital assets.
Asset-Specific Console
Access a tailored console for each asset, streamlining management and control. Efficiently address vulnerabilities and unique security aspects with a focused and intuitive interface.
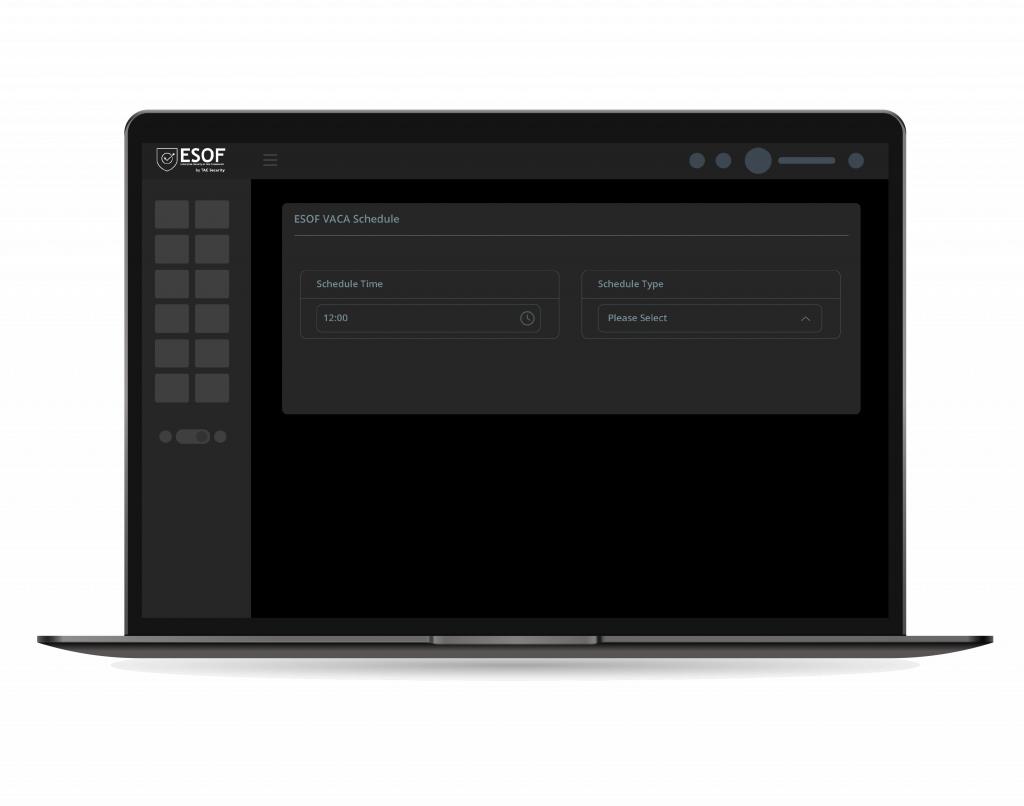
Ad-hoc and Scheduled Scans
Choose flexibility in vulnerability assessments. Initiate immediate ad-hoc scans for on-the-spot insights or schedule automated scans for consistent, routine evaluations. Keep your IT infrastructure secure without manual effort.
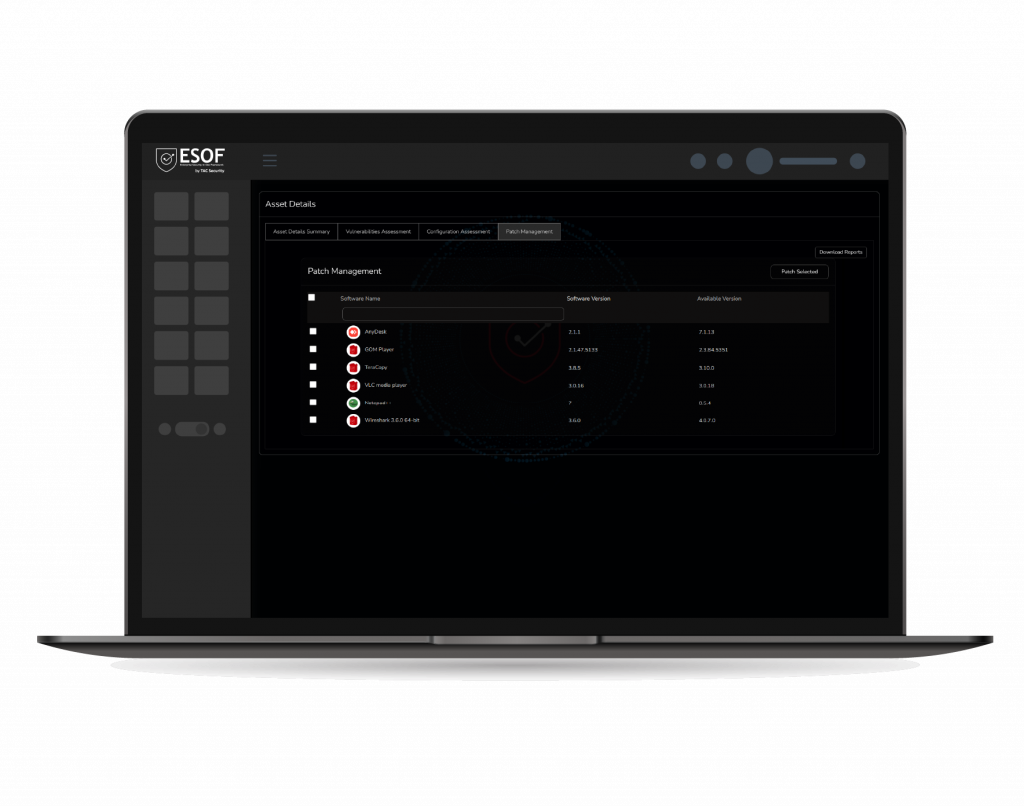
Automated Patch Management
ESOF VACA, Automated Patch Management streamlines the identification and deployment of software patches, ensuring efficient and automated security updates to enhance system resilience and minimize manual efforts.
Next Generation Vulnerability Management is the need of the hour.
Try ESOF VACA for free Today!
World’s Top Brands Trust Us!






