There are several steps that businesses can take to enhance their cybersecurity posture. These include implementing robust firewalls, anti-virus software, and intrusion detection and prevention systems and ensuring that all software and applications are up-to-date and adequately patched. Educating employees on basic cybersecurity practices such as strong password management, avoiding phishing scams, and safe browsing habits is also essential.
In addition, regular vulnerability assessments and penetration testing can help identify and address weaknesses in a company’s security infrastructure before malicious actors can exploit them. A comprehensive incident response plan that outlines the steps to be taken in a security breach can also help minimize the damage caused by such an event.
In today’s digital age, cybersecurity is not an option but necessary for businesses of all sizes. By investing in a robust cybersecurity strategy, companies can protect their sensitive information, maintain the trust of their customers, and safeguard their financial well-being.
Vulnerability Assessment and Penetration Testing (VAPT): An Overview
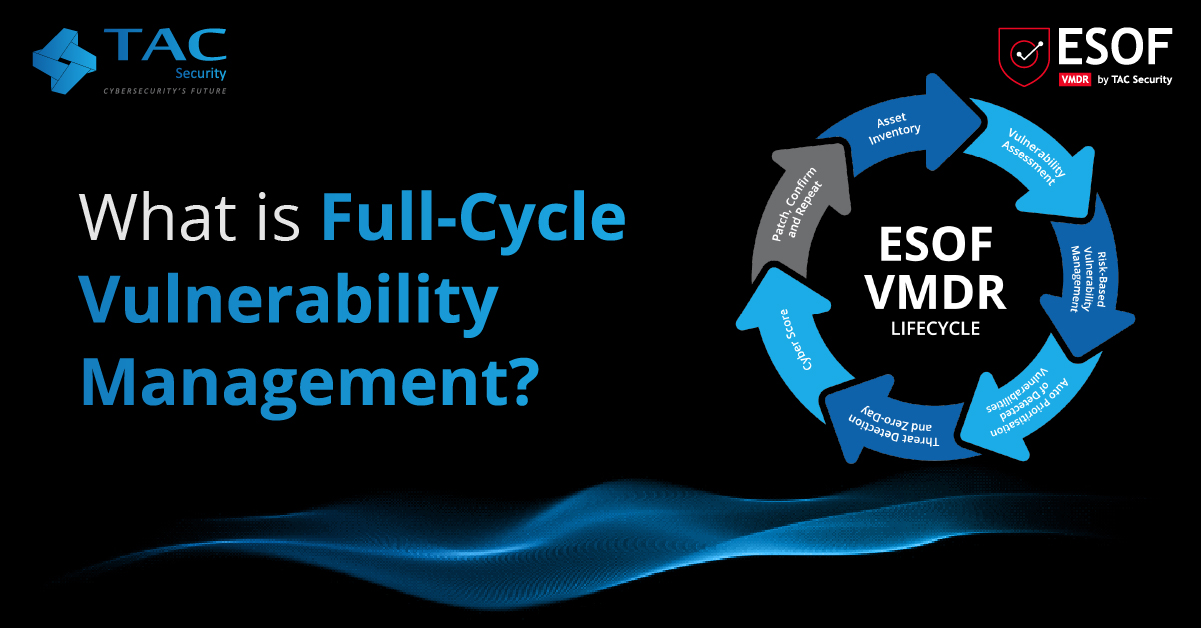
Vulnerability Assessment and Penetration Testing (VAPT) identifies security weaknesses in software applications, systems, and networks. It typically involves two parts:
- Vulnerability Assessment: Identifying and evaluating security vulnerabilities in a system or network. It involves using automated tools to scan for known vulnerabilities and potential weaknesses in the system. A vulnerability assessment aims to identify and prioritize potential security risks so that they can be addressed before attackers exploit them.
- Penetration Testing: “pen testing” exploits the vulnerabilities identified during the vulnerability assessment. Penetration testing typically involves manually testing the system or network using the same techniques that attackers might use to gain unauthorized access. A penetration test aims to simulate an attack, identify potential weaknesses in the system’s defenses, and provide recommendations for addressing those weaknesses.
A vulnerability analysis tool identifies vulnerabilities without distinguishing between defects that may result in loss and those that will not. An organization’s vulnerability scanner should alert them to any pre-existing faults in the configuration of its system and help them find them. Penetration tests find exploitable defects and determine their severity.
Cybersecurity and VAPT Services
IoT and mobile applications have become more vulnerable due to technology adoption. Under ESOF AppSec, we have VAPT services that users can use to verify their enterprise-level security against real-world threats, understand the risks associated with the network and system, and assess their consequences. We have VAPT services where our security engineers do the manual pen testing of the applications and eliminate false positives.
VAPT is a comprehensive approach that involves identifying potential vulnerabilities in the network, testing the effectiveness of the security controls, and then performing penetration testing to simulate an attack to identify any weaknesses in the system.
By conducting VAPT services, organizations can identify and fix vulnerabilities in their security systems, which can help prevent attacks by hackers and other malicious actors. It can also help organizations comply with regulatory requirements and demonstrate their commitment to security to their customers and clients.
TAC Security’s VAPT services play an essential role in protecting organizations from cyber threats and ensuring the reliability and robustness of their security systems.